Introduction
In today's fast-paced cloud-native ecosystem, automating the deployment of Kubernetes clusters is critical for ensuring scalability, repeatability, and reliability. This blog presents a comprehensive Ansible-based automation framework designed to simplify and accelerate the provisioning of highly available Kubernetes clusters on RHEL 8 environments.
Ansible stands out as the ideal orchestration tool for Kubernetes deployment due to its agentless architecture, idempotent execution model, and declarative YAML syntax that aligns perfectly with Kubernetes' own configuration paradigm. By leveraging Ansible's powerful automation capabilities, we can transform complex, error-prone manual deployments into consistent, repeatable processes.
The playbooks included in this solution automate the complete lifecycle of Kubernetes cluster creation—from setting up high availability using HAProxy and Keepalived with a Virtual IP (VIP), to installing Kubernetes across both control plane and worker nodes. Beyond cluster deployment, the playbooks also integrate essential services and workloads, enabling the cluster to be fully functional out of the box.
Whether you're an infrastructure engineer, DevOps practitioner, or AI/ML architect, this automation toolkit empowers you to deploy production-grade Kubernetes clusters with minimal manual intervention and maximum consistency.
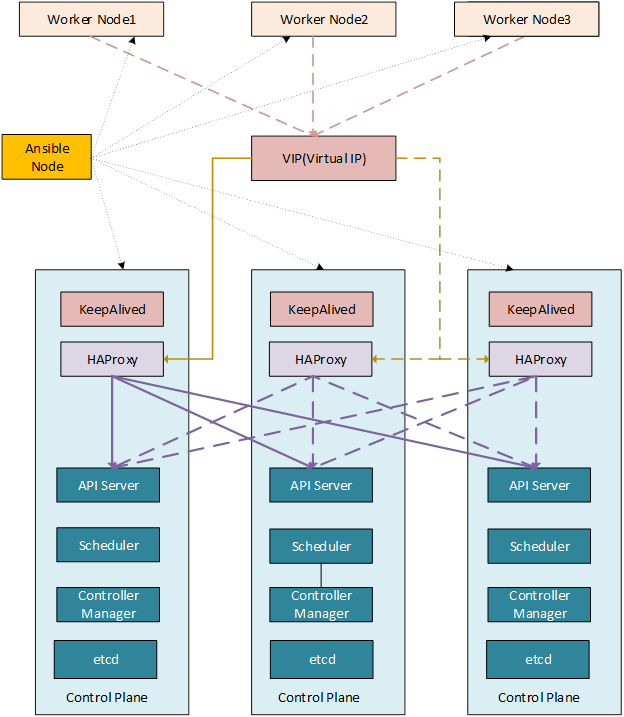
Architecture Overview
Our automated deployment establishes a highly available Kubernetes architecture with:
· Multiple control plane nodes for redundancy
· HAProxy load balancer with Keepalived for automatic failover
· Virtual IP (VIP) that follows the active HAProxy instance
· Antrea CNI for cluster networking
· Persistent storage through Local Path Provisioner
· Multiple worker nodes for distributed workloads
Here’s a high-level flowchart for deploying a Kubernetes (K8s) cluster using Ansible:
Key Features
· Highly Available Architecture
Configure HAProxy and Keepalived to enable high availability with automatic failover using Virtual IP.
· Modular Kubernetes Deployment
Install and configure Kubernetes components—kubelet, kubeadm, kubectl—on both control plane and worker nodes.
· Integrated Services Deployment
Seamlessly deploy critical services like:
· Jupyter Notebook for interactive data science and AI workloads.
· MinIO for S3-compatible object storage.
· Local Path Provisioner for persistent volumes.
· PostgreSQL as a stateful backend database.
Prerequisites
Before running the playbooks, ensure the following:
· Ansible 2.10+ is installed on your control machine
· Passwordless SSH access is configured for all target servers (Control and Worker nodes)
· Target servers are running RHEL 8 (tested on RHEL 8.6+)
· Target servers are registered with Red Hat Subscription
· Your inventory and variable files are properly configured
· Network connectivity between all nodes (control plane and workers)
· Firewall allows necessary Kubernetes ports (6443, 2379-2380, 10250-10252)
Cluster Deployment Guide
For detailed step-by-step instructions on deploying the Kubernetes cluster—including repository cloning, inventory setup, variable configuration, playbook execution, and cluster verification—please refer to the official Hitachi Vantara's GitHub. These Ansible playbooks have been validated on Hitachi Vantara servers and are optimized for high availability and reliability in production environments.
These instructions walk you through:
· Installing CRI-O and Kubernetes packages
· Setting up high availability with HAProxy and Keepalived
· Initializing control plane nodes and joining worker nodes
· Deploying integrated workloads
· Verifying the Cluster and performing teardown operations.
Refer to README to ensure smooth deployment tailored to your environment.
Benefits of This Automation:
· Consistency: Eliminates manual errors across repeated deployments
· Efficiency: End-to-end setup in minutes
· Production-Ready: Suitable for dev/test as well as enterprise-grade environments
Troubleshooting Common Issues
Node Join Failures
If worker nodes fail to join the cluster:
· Verify network connectivity between worker and control plane nodes
· Check firewall settings to ensure ports 6443 and 10250 are open
· Examine the kubelet logs: journalctl -u kubelet
· Regenerate the join command and token if expired: kubeadm token create --print-join-command
HAProxy/Keepalived Issues
If the Virtual IP fails to function properly:
· Check interface configuration in vars.yaml
· Verify HAProxy status: systemctl status haproxy
· Check Keepalived logs: journalctl -u keepalived
· Test manual VIP assignment to isolate networking issues
Container Runtime Issues
If containers fail to start:
· Verify CRI-O service: systemctl status crio
· Check CRI-O logs: journalctl -u crio
· Verify connectivity to container registries
· Try manually pulling an image: crictl pull nginx:latest
Summary
This Ansible-based Kubernetes automation framework offers a robust, repeatable, and scalable solution for provisioning highly available clusters on RHEL systems. With built-in support for key services and a flexible design, it accelerates infrastructure readiness for containerized workloads in AI/ML, data engineering, and microservice-based applications.
By embracing infrastructure-as-code principles and comprehensive automation, your team can focus on developing and deploying applications rather than managing the underlying infrastructure. This framework serves as a foundation that can evolve alongside your containerization journey.
References
· Kubernetes Documentation
· Ansible Documentation
· HAProxy Documentation
· CRI-O Documentation
· Antrea CNI